In the previous posts, we explored the tension between the unconstrained and constrained visions and how a Kubernetes-based platform with guard rails offers a balanced approach. Now, let’s dive deeper into the practical aspects of securing this platform by incorporating advanced security controls. Specifically, we’ll discuss the concept of container signing and how Kubernetes code, such as the Admission Controller, can guarantee that only verified and secure containers are deployed in an environment.
The Role of Security in a Kubernetes Platform
Security is paramount in any technology environment, but it becomes even more critical when dealing with a complex, scalable platform like Kubernetes. As organisations increasingly adopt Kubernetes, the need to enforce robust security practices has never been more significant. One of the most effective ways to enhance security is by implementing container signing—a process that verifies the integrity and authenticity of your containers before they are allowed to run in your cluster.
Container Signing: The Basics
At its core, container signing can signal that an organisation has vetted and approved each container image deployed in a Kubernetes environment. This is achieved by signing the container during the build phase, typically within the CI/CD pipeline. The signing process generates a cryptographic signature stored alongside the container in an OCI-compliant container registry.
Tools like Cosign, part of the Sigstore project, provide a straightforward way to sign containers. The signature acts as a stamp of approval, indicating that the container has passed all necessary security checks, including static analysis, secret detection, and other vulnerability assessments, possibly even AI detection.
Note: The Sigstore project contains many other tools that can be used in collaboration to perform many more valuable functions and operations. In the environment described, only a few features for ease of use and simplicity were used to solve the most pressing problems. Far more is possible.
Implementing Security Controls in the CI/CD Pipeline
Let’s walk through a typical workflow:
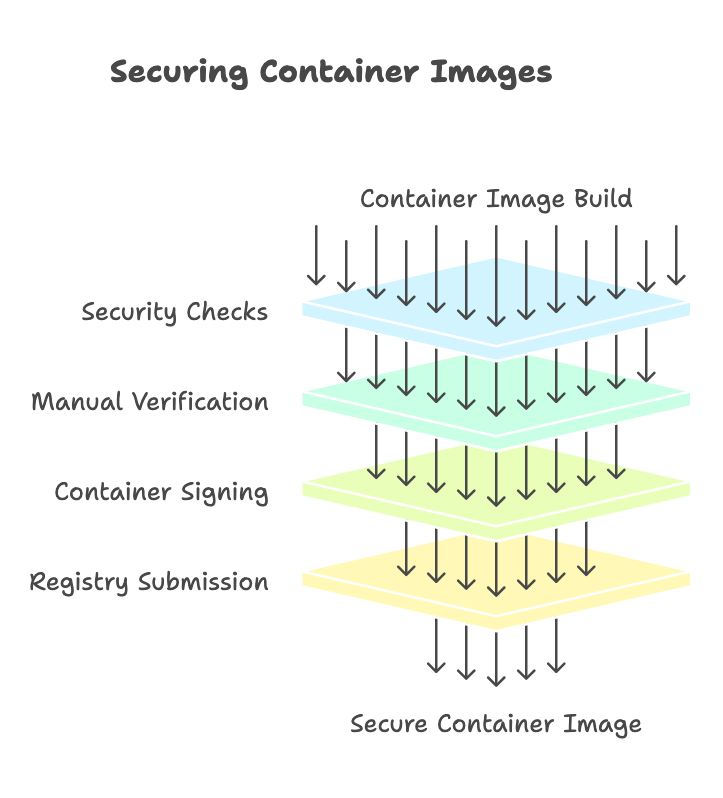
- Build Phase—A developer builds a container image for their application. This image is pushed through a CI/CD pipeline, often using tools like GitHub or GitLab, examples of DevOps platforms.
- Security Checks—Before the container can be signed, it must pass a minimum number of security checks. These checks may include Static Application Security Testing (SAST) to analyse the code for vulnerabilities, secret detection to ensure no sensitive credentials or keys are embedded, and other security measures tailored to your organisation’s needs. Passing helps to show a reduced risk with the scanned service.
- Manual Verification—In some cases, additional manual checks may be required. This step can involve peer reviews or security team approval to ensure the container meets the required standards, patterns, or architectures. In some organisations, external regulatory or compliance requirements may also be baked into the process.
- Container Signing—The container is ready to be signed once all checks are complete. Signing involves generating a cryptographic signature using a secure private key, typically stored in a vault service like HashiCorp Vault. This key is kept safe and is only accessible to the signing service, which is a custom API managed by a Platform or Operational team.
- Registry Submission: The signed container is then pushed back to the container registry, where it is stored alongside its unsigned counterpart. This separation allows for the unambiguous identification of containers approved for deployment.
Admission Control: Ensuring Compliance at Deployment
The final puzzle piece is Kubernetes Admission Control, a crucial security feature that acts as a gatekeeper for the K8s cluster. So, what is an Admission Controller (AC), and how does it function?
An AC is a mechanism that intercepts requests sent to the Kubernetes API server before they are saved as objects in the cluster. This interception occurs after the request has been authenticated and authorised but before it is persisted. There are two primary types of ACs: mutating and validating. Mutating controllers can modify the objects they admit by adding labels or annotations. Validating controllers ensure that requests meet specific policies without altering the objects themselves.
These controllers are vital in controlling what can be created, modified, or deleted within the cluster. They are significant when enforcing security policies, such as ensuring that only signed and approved containers are deployed.
How Admission Control Works
When a developer submits a request to deploy a container in Kubernetes, the admission control process is triggered. This process develops in two main stages:
- Mutating Phase: First, mutating admission controllers are executed. These controllers can adjust the object being created or modified to meet the required policies, such as injecting metadata or enforcing naming conventions.
- Validating Phase: After any necessary mutations, validating admission controllers take over. They assess whether the object complies with all predefined security and compliance policies. If any part of the request fails this validation, the entire request is denied, and an error is returned to the user.
In our context, the validating admission controller is essential for enforcing container signing. Before a container can be deployed, the controller verifies its cryptographic signature against a set of authorised public keys. This verification process ensures that only containers signed by the trusted entity are permitted to run in the cluster. The deployment is blocked if the signature is invalid or missing, safeguarding the environment from potentially harmful or unauthorised code.
Integrating admission control and container signing into your Kubernetes platform creates a more secure and compliant environment, reducing risks and ensuring that all deployments adhere to the organisation’s security standards.
For more detailed information about admission controllers, you can refer to the Kubernetes documentation.
Conclusion: Strengthening Your Kubernetes Platform
Integrating container signing and Admission Control into your Kubernetes platform effectively creates a more secure and compliant environment. While it’s impossible to guarantee complete protection against all attacks—short of shutting down your environment entirely, which is impractical for most businesses—this approach significantly mitigates risks associated with running applications, particularly those exposed to the internet for customer or staff use. By applying rigorous standards and automated security checks, you can reduce potential attack vectors and ensure that all containers meet the required security standards before deployment, ultimately streamlining the development process and enhancing overall security.
In summary, a well-implemented security strategy within your Kubernetes platform empowers your teams to innovate while maintaining the highest levels of security and compliance. As we continue to explore the possibilities of platform engineering, it’s clear that security is not an afterthought but a fundamental pillar of success.
Stay tuned for future blog posts, where we’ll explore further ways to optimise your Kubernetes platform and enhance your organisation’s ability to deliver secure, high-quality software at scale.
Thanks for reading!